NIST 800-218 Software Development Framework
-
NIST 800-218 (SSDF)
Secure Software Development Framework
NIST 800-218 SSDF
NIST 800-218, also known as the Secure Software Development Framework (SSDF), provides guidelines and best practices for integrating security into the software development lifecycle (SDLC). Published by the National Institute of Standards and Technology (NIST), this framework is designed to help organizations produce software that is secure by design, reducing vulnerabilities and improving resilience against attacks.
- Prepare the Organization (PO):
- Establish security practices and governance for software development.
- Ensure roles, responsibilities, and policies are clearly defined.
- Integrate security training for development teams.
- Protect the Software (PS):
- Implement security controls during the development process.
- Use tools like static and dynamic analysis to identify vulnerabilities.
- Manage security risks for third-party software and components.
- Produce Well-Secured Software (PW):
- Implement coding practices that ensure secure design and functionality.
- Regularly test and review the code for vulnerabilities.
- Employ secure coding standards and automated security testing tools.
- Respond to Vulnerabilities (RV):
- Establish processes for handling and responding to discovered vulnerabilities.
- Implement patch management and updates to address security gaps.
- Coordinate with stakeholders to mitigate risks from vulnerabilities.
Sample of tasks organized by Groups and Practices:
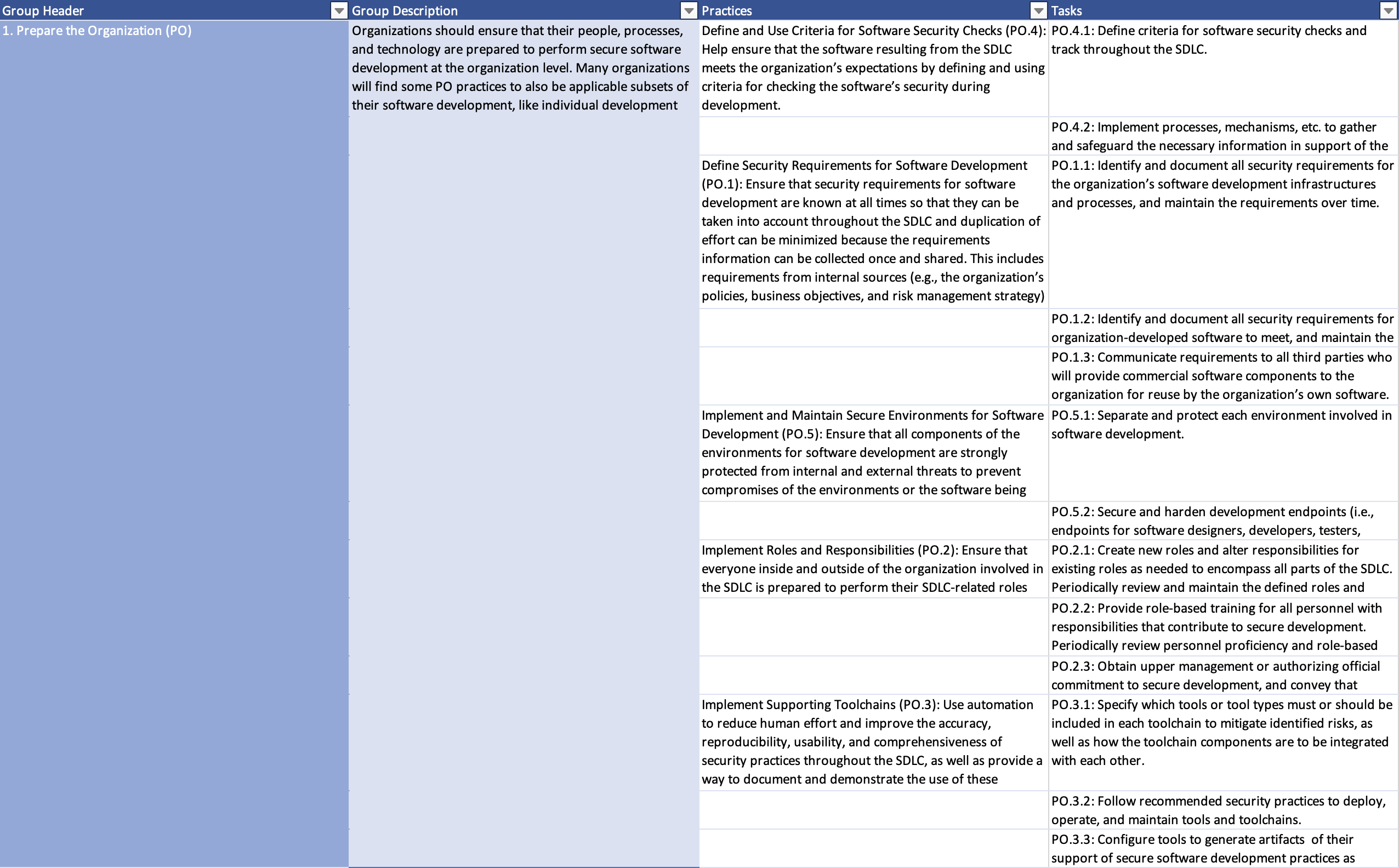
A full list of tasks mapped to practices can be found here. For a download of the spreadsheet in Excel (.xlxs format), email: [email protected]
Who does it apply to?
NIST 800-812 SSDF is essential for various organizations, particularly those developing or managing software supply chains.
-
Software Development Organizations
- In-house Development Teams: Organizations that build software internally should use NIST 800-218 to integrate security into their development processes, ensuring their applications are secure by design.
- Software Vendors: Companies that produce software products for other businesses or consumers must adhere to secure development practices to maintain trust and avoid security issues that could harm their reputation.
-
Organizations in Regulated Industries
- Finance, Healthcare, and Government Sectors: These industries often have strict compliance requirements related to data security and privacy. Implementing the SSDF helps organizations demonstrate that they are following best practices, which may be required by regulations like HIPAA, GDPR, or PCI-DSS.
- Critical Infrastructure (e.g., Energy, Transportation): Security vulnerabilities in software used by critical infrastructure can lead to significant disruptions. NIST 800-218 helps ensure that software development in these sectors is secure and resilient.
-
Federal Agencies and Contractors
- U.S. Federal Government: Agencies are required to follow NIST standards, including 800-218, to ensure the security of their software. This is part of a broader effort to strengthen the cybersecurity posture of the federal government.
- Government Contractors: Companies that develop software for the federal government must comply with NIST standards, including 800-218, to meet contractual obligations and ensure they can continue working with federal clients.
-
Organizations Managing Third Party Software
- Enterprises Using Third-Party Software Solutions: Many organizations rely on software developed by third parties. NIST 800-218 can help these organizations set standards and requirements for the software they acquire, ensuring vendors follow secure development practices.
- Managed Service Providers (MSPs): MSPs that develop, deploy, or manage software solutions for clients should use the SSDF to ensure the security of the applications they handle, reducing the risk of vulnerabilities that could impact multiple customers
-
Any Organization Seeking to Enhance Cybersecurity Posture
- Startups and SMBs: Smaller companies, particularly those with limited security expertise, can benefit from adopting NIST 800-218 to establish secure development practices from the outset.
- Enterprises with Digital Transformation Initiatives: As organizations move towards more software-driven models, integrating security into software development is crucial to avoid introducing vulnerabilities.
How can Socium Security help?
Socium Security can provide companies of all sizes an independent program maturity assessment based on the NIST CSF using a standard methodology. This service is typically paired with a Security Architecture Assessment that includes an assessment, report, and risk-based recommendations around the IT architecture, data processing, and security controls in place. Together, this provides management and technical stakeholders a complete picture of the current state security posture.
If your cybersecurity practices are operating with measurable maturity, consider testing the program’s capabilities with a crisis management exercise or penetration test by Socium Security