The growing market for technology to support security programs is creating a more complex situation for many of our clients to navigate. Part of this is due to the many use cases that the marketplace is addressing, and the specific use cases that they are supporting. We recommend that buyers consider the maturity of their programs, and the following list of capabilities in order to narrow the search;
- Assessments – Ability to conduct assessments at different levels in the organization depending on business unit, computing environment, etc.
- Program Maturity Assessments
- Vendor Assessments
- Risk Assessments
- Roadmap and planning – Ability to establish a prioritized roadmap of remediation and steady-state activities and track status over time.
- Document / Policy Management – Ability to produce and manage Policy and Process documentation.
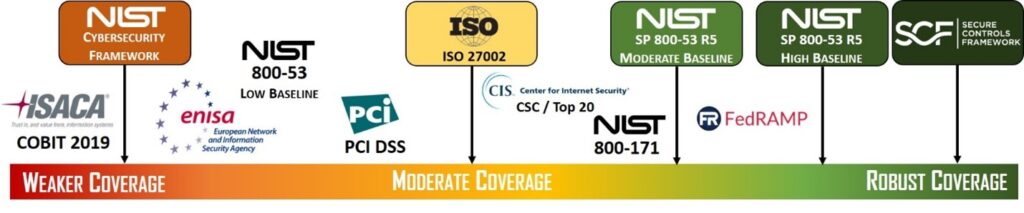
- Controls Management / Compliance – Ability to upload and manage evidence of control compliance to recognized frameworks and regulations (NIST, ISO, PCI DSS, CMMC , etc.), and/or automate the evidence collection
- Workflow and automation – Ability to integrate with external business systems and trigger workflow
- Data reporting and analysis – Ability to present real-time data and visualizations including the ability to click into objects to understand source data.
Questions to consider
What is the organization’s motivation for GRC technology?
Determining what or who is driving the need for GRC technology and why can help clarify and narrow the marketplace of options. Typically, there are a few primary reasons;
- An event / incident like a data breach has occurred.
- The current solution can no longer support the program requirements.
- An executive or board member requested the project.
How are you going to support the GRC Platform?
A GRC platform should integrate with your organization’s technology, processes, and people resources. Refining how you expect to support the technology will help the selection and ongoing operation.
- Internal IT / GRC resources
- Existing partners or consultants
- A combination of internal and partner resources
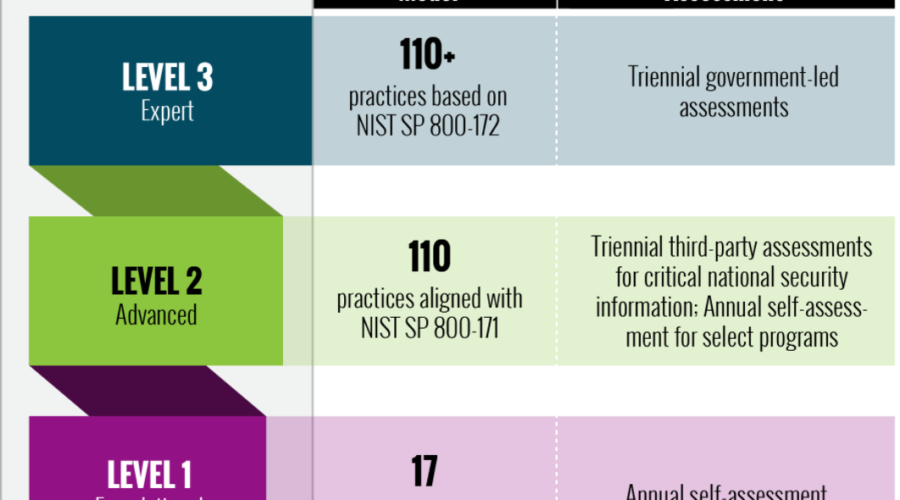
Where are you now with program maturity and what is your target?
Program maturity is a primary consideration of how GRC and security program management tools should be selected. Depending on the complexity and maturity of the organization’s security program, the requirements will shift to specific players in the market. The following maturity descriptions can be used to narrow the best vendors for your needs:
Initial
Programs that are early in their development and operation, have simple compliance requirements, and limited support resources.
- Provide Policy templates and control mappings aligned to standards (NIST, ISO, SOC2, etc.)
- Provide surveys to assess and report on control implementations
- Provide vendor assessment workflow and reporting
- Provide ability to assess and report on risks
For programs that are in the “Initial” state of maturity, the following options should be considered; OneTrust, MyCISO, Drata, Logicgate
Established
Programs that are designed and aligned to business needs, have some documented / repeatable processes, but limited support resources.
- Provide workflow to support process implementations
- Provide roadmaps to plan annual cycles and reporting
- Improve awareness of control owner responsibilities, documentation, and implementation support
For program that are “Established” and looking to advance, the following options are suitable; OneTrust, Drata, Vanta, Riskonnect, Fusion, CyberSaint, ZenGRC
Mature
Programs that have documented and repeatable processes, an adequate level of support resources, and defined business alignment demonstrated over a few annual cycles of improvement. Mature programs will typically have the following objectives:
- Increase program efficiency through automation and workflow APIs
- Improve risk decisions through data analytics
- Increase collaboration across stakeholders and departments with role based access (IT, Risk Management, Legal, Compliance, Executive Management)
For the “Mature” programs, the following vendors are worth consideration; RSA Archer, MetricStream, ServiceNow GRC, SAI Global
Pricing
Most tools in this space are priced by the user count and number of control frameworks required. Larger platforms also charge for the number of modules so that the solution can scale with the customer’s need.
Services Offered
Socium Security can provide advisory services to establish the security program foundation and assist with GRC evaluation and selection projects to support the program. Socium can also provide support services to manage the ongoing operation of the GRC platform