In the world of football, victory is achieved through meticulous planning, discipline, and teamwork. The same principles apply to cybersecurity. At first glance, these two fields might seem worlds apart, but a closer look reveals striking similarities in their foundational strategies. Whether you’re protecting your end zone or your organization’s data, success hinges on a strong defense, adaptability, and constant vigilance. Let’s explore how the fundamentals of football can provide valuable lessons for robust cybersecurity.
1. The Game Plan: Strategy and Preparation
In football, a well-thought-out game plan is essential. Coaches analyze opponents, anticipate their moves, and devise strategies to counter them. Similarly, in cybersecurity, preparation is key. Organizations must understand their threat landscape, identify vulnerabilities, and develop a comprehensive strategy to protect their assets. Just as a football team studies game tapes to anticipate plays, cybersecurity teams must conduct regular risk assessments, threat modeling, and scenario planning to stay ahead of potential attacks.
2. The Defensive Line: Perimeter Security
A football team’s defensive line is its first line of defense, tasked with stopping the opposing team from advancing. In cybersecurity, perimeter security serves the same purpose. Firewalls, intrusion detection systems, and antivirus software form the initial barrier against cyber threats. Just as a defensive line needs to be strong and impenetrable, so too must an organization’s perimeter defenses be robust and up-to-date, capable of thwarting the majority of threats before they reach critical systems.
3. Linebackers and Safeties: Monitoring and Incident Response
Linebackers and safeties are responsible for monitoring the field and reacting quickly to threats that breach the defensive line. In cybersecurity, this role is mirrored by monitoring systems and incident response teams. These elements are crucial for detecting suspicious activity and responding to breaches in real-time. Like football players reading the offense’s moves, cybersecurity professionals must be adept at recognizing and reacting to signs of an attack, mitigating damage before it escalates.
4. Teamwork and Communication: Coordination Across the Organization
Football is a team sport where success relies on seamless coordination between players. Each member must understand their role and communicate effectively to execute plays. The same is true for cybersecurity. Effective cybersecurity requires a collaborative effort across the entire organization. From IT teams to executives, every stakeholder must understand their responsibilities and maintain open lines of communication. Just as miscommunication on the field can lead to a touchdown, breakdowns in communication within an organization can lead to successful cyberattacks.
5. Adapting to the Opponent: Continuous Improvement
In football, teams must adapt their strategies throughout the game. Halftime adjustments based on the opponent’s tactics can make the difference between winning and losing. Cybersecurity operates under the same principle of continuous improvement. Cyber threats are constantly evolving, and organizations must stay agile, regularly updating their defenses, and learning from past incidents. Just as a football team reviews its performance after each game, cybersecurity teams should conduct post-incident analyses to improve their defenses and response strategies.
6. The Playbook: Policies and Procedures
Every football team has a playbook—a collection of strategies, plays, and tactics designed to lead them to victory. In cybersecurity, the playbook consists of policies, procedures, and guidelines that govern how an organization protects its information assets. These documents outline best practices for data protection, user access, and incident response, ensuring that everyone in the organization knows their role in maintaining security. A well-crafted playbook is essential for both football teams and cybersecurity teams alike, providing a clear path to success.
7. The Goal Line: Achieving Success
In football, the ultimate goal is to score points and win the game. In cybersecurity, the goal is to protect the organization’s data and maintain its integrity, availability, and confidentiality. While the stakes are different, the fundamentals of achieving success are remarkably similar. Both football teams and cybersecurity teams must remain disciplined, vigilant, and adaptable, constantly working to improve their strategies and defenses.
Football teams and Cybersecurity teams are more similar than you think…
Whether on the football field or in the world of cybersecurity, the fundamentals of success remain the same: preparation, strong defense, teamwork, and adaptability. By applying the lessons learned from football, organizations can build a cybersecurity program that is not only resilient but also capable of evolving in the face of new challenges.
At Socium Security, we understand the importance of these fundamentals. We help organizations develop tailored cybersecurity strategies that reflect the unique needs of each business and support the operation of the required practices and capabilities. Football and cybersecurity both take a team to be successful.
—
By drawing parallels between football and cybersecurity, this blog post highlights the importance of preparation, defense, teamwork, and adaptability in achieving success in both fields. It’s designed to resonate with readers by using familiar concepts to explain complex cybersecurity strategies, making the content more engaging and relatable.
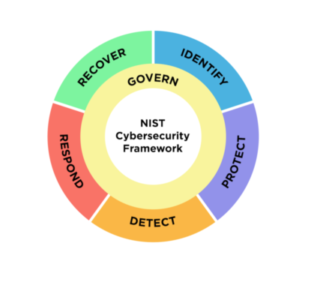
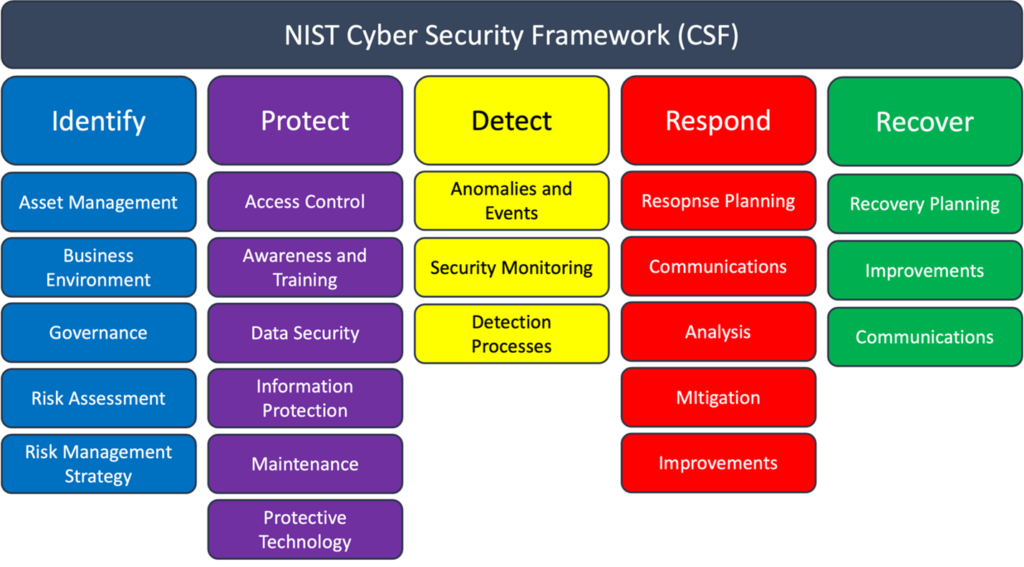
Refer to the NIST CSF 2.0 Govern and Identify functions to start organizing your approach and strategy.
If your cybersecurity practices are operating with measurable maturity, consider testing the program’s capabilities with a crisis management exercise or penetration test by Socium Security.